Navigating website security can feel like walking through a dangerous area with hidden threats. One of the most concerning risks are zero-day vulnerabilities. These are secret flaws in software or systems that developers, users, and even security experts don’t know about yet.
But don’t worry! In this guide, we’ll explain what zero-day vulnerabilities are, why they matter for your website’s security, and how you can protect your site from these potential attacks.
Understand Zero-Day Vulnerability
A zero-day vulnerability is like discovering a hidden trapdoor in your favorite game—except it’s much more serious because it’s in widely used software. Imagine there’s a flaw or hole in a software program that no one knows about yet—not the developers, users, or even the security experts who hunt for such issues.
The term “zero-day” means that developers have “0 days” to fix the problem. By the time they find out about it, hackers might have already discovered and exploited it. It’s like trying to repair a leaky boat after it has already sunk—there’s no time to act, and the damage can be severe.
In simpler terms, imagine you’re playing a video game without knowing there’s a hidden trap. Someone finds it and starts using it to their advantage, causing problems or gaining unfair advantages.
Zero-day vulnerabilities are a major concern for website owners, developers, and anyone using software because they strike suddenly and unexpectedly, causing potential chaos before anyone even realizes they exist.
The Role of Vulnerability Researchers
Think of vulnerability researchers as the detectives of the digital world. They search for these hidden flaws—not to exploit them, but to find and fix them. Their work is crucial in keeping our digital spaces safe and secure.
Ready for a closer look? Let’s dive into an example to see how zero-day vulnerabilities work.
Zero-Day Vulnerability Example
Imagine you’re the only person maintaining a premium WordPress plugin used by a small group of users. You recently released an update that accidentally introduced a vulnerability.
Here’s the catch: Your plugin hasn’t been reviewed by other developers, and neither your manual nor automatic tests caught the flaw. Also, none of your users checked the new code. As a result, the vulnerability goes unnoticed and remains hidden in the plugin.
Is this a zero-day vulnerability? Yes, it is!
If a hacker discovers this flaw, they won’t focus on fixing it. Instead, they’ll exploit it for their own benefit. This scenario reflects real-world situations where zero-day vulnerabilities pose a serious risk to websites.
When attackers find a security issue before the developers, users, or security researchers, the potential for damage increases rapidly—until a fix is available.
Understanding and quickly addressing zero-day vulnerabilities is essential for protecting websites and reducing the harm from cyber threats.
What Makes Zero-Day Vulnerabilities Attractive to Hackers?

Zero-day vulnerabilities are like treasure for hackers. These are hidden security flaws in software that haven’t been fixed yet, giving attackers a chance to exploit them. Some of these vulnerabilities need special permissions to be used, while others can be exploited by anyone who knows how.
Attackers are always on the lookout for these flaws. They test websites to see if they have specific vulnerabilities. To make things even harder, they use automated tools to scan the internet for weak spots. These tools help them search a large number of websites quickly, looking for ones they can exploit.
Discover How Zero-Day Vulnerabilities Are Exploitated
Hackers take advantage of zero-day vulnerabilities with skill and precision. These are flaws in software or systems that developers and users don’t yet know about, leaving them open to attack. Hackers use their expertise and advanced tools to exploit these weaknesses before a fix is available, gaining unauthorized access and causing damage.
Here’s how hackers typically exploit zero-day vulnerabilities:
- Malicious Code: They might inject harmful code into systems to disrupt or take control.
- Phishing Attacks: They deceive users with fake emails or messages to trick them into revealing sensitive information.
- Advanced Persistent Threats (APTs): They use sophisticated techniques to maintain long-term access to compromised systems.
Exploiting a zero-day vulnerability is like a race against the clock. Hackers aim to act before the flaw is discovered and patched, using the element of surprise to launch their attacks and avoid detection.
Stages of zero-day vulnerability:
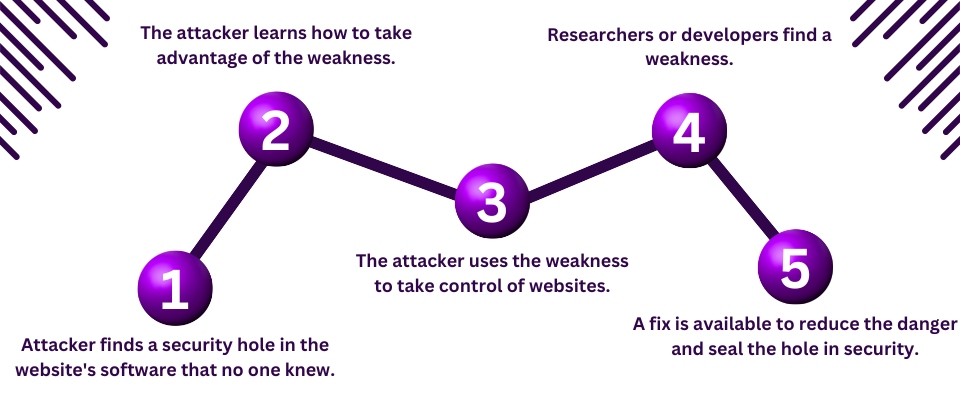
How to Make Your Site Safe From Zero-Day Vernerability
To guard against zero-day vulnerabilities, a strong security approach is essential. Here’s how you can protect your website:
- Keep Software Updated: Regular updates often include patches for newly discovered vulnerabilities. Keeping your software up-to-date closes potential security gaps.
- Use Strong Passwords: Strong, unique passwords make it harder for attackers to gain unauthorized access to your systems.
- Limit Third-Party Plugins: While plugins can add functionality, they can also introduce risks. Use only trusted plugins and minimize their use to reduce vulnerabilities.
- Choose Secure Hosting: Opt for a hosting provider with strong security measures. A secure hosting environment helps protect your site from various attacks, including zero-day exploits.
- Implement Security Controls:
- Web Application Firewalls (WAFs): These tools analyze incoming traffic and block suspicious behavior before it can harm your site.
- Intrusion Detection Systems (IDS): IDS alert you to unusual activity that could indicate a potential breach.
Even with the best defenses, zero-day vulnerabilities can sometimes slip through. That’s why ongoing research and vigilance are crucial. Our team at ElySpace constantly monitors emerging threats and updates security protocols to stay ahead of attackers. For top-notch protection, visit ElySpace and secure your website today!
Conclusion

Zero-day vulnerabilities are among the most elusive and dangerous cyber threats, hidden in software and systems and waiting for malicious actors to exploit them. But with the right knowledge and proactive measures, you can protect your website from these hidden dangers.
Here’s how to fortify your defenses:
- Understand Zero-Day Vulnerabilities: Know what they are and how they can impact your systems.
- Adopt Best Security Practices: Regular updates, strong passwords, and careful use of plugins help close security gaps.
- Implement Robust Defenses: Use tools like Web Application Firewalls (WAFs) and Intrusion Detection Systems (IDS) to monitor and protect against threats.
Staying vigilant is crucial. Keep informed, stay updated, and be proactive in your cybersecurity efforts. By doing so, you can protect your online presence and navigate the digital world with confidence.

