Web shells represent a severe threat to the security of websites, hence you need to know about Web Shell Defense: Types, Mitigation and Removal. These sneaky little scripts are like secret doors that malicious hackers use to sneak into compromised web servers. Once they’re in, they can wreak havoc by running commands and controlling the server from afar. They usually find their way in through vulnerabilities like SQL injection, remote file inclusion (RFI), or cross-site scripting (XSS).
Imagine having an unwelcome guest who can come and go as they please, messing with your stuff and causing chaos whenever they feel like it. That’s what a web shell does to a website once it’s deployed. It’s like giving a stranger the keys to your house and letting them do whatever they want inside. They could steal your valuables, mess up your place, or even invite more troublemakers over.
What’s worse, web shells are pretty crafty. They can be written in different programming languages like PHP, Python, Ruby, ASP, Perl, or Bash, making them versatile and adaptable to different environments. This means they can hide in plain sight, making them hard to spot and even harder to get rid of.
In fact, according to recent data, more than 12% of hacked websites had at least one web shell lurking around when they were cleaned up last year. That’s a scary thought! It shows just how big of a problem web shells are and why it’s crucial to understand and deal with them.
So, what can you do to protect your website and your visitors from these pesky intruders? That’s where this article comes in. We’re here to give you the lowdown on web shells: how they work, the risks they pose, and the best ways to sniff them out and kick them to the curb.
By learning about web shells and how to deal with them, you can safeguard your website and keep those sneaky hackers at bay. After all, when it comes to web security, knowledge is power!
What is a Web Shell?
A web shell is like a hidden doorway for hackers into a website. It’s a bad piece of code they put on a website they’ve already broken into. Once it’s in place, the hackers can control the website from afar, kind of like using a remote control. They can do all sorts of things, like giving commands to the website’s server, changing files, and peeking into databases. Basically, it gives them secret access to the whole system without permission.
How does a web shell get on a website or server?
Web shells sneak onto your website or server when attackers find a way to break in without permission. Here are some common ways they do it:
- Cross-Site Scripting (XSS): Hackers take advantage of weak spots in websites to slip in harmful scripts. These scripts can then take over the connection between the user and the site, opening the door for attacks.
- SQL Injections: By injecting malicious SQL statements into a database, attackers can manipulate it, run commands on the server, and sometimes get their hands on sensitive information.
- Server Misconfigurations: If server settings aren’t set up correctly, attackers can exploit these mistakes to gain access they shouldn’t have.
- File Processing and Upload Vulnerabilities: Weaknesses in how files are handled and uploaded to a server let attackers slip in files containing web shells. Once uploaded, these files can be activated to take control.
- Remote Code Execution Vulnerabilities: If there’s a flaw that lets attackers run their own code on the server, they can use it to plant web shells and take control.
- File Inclusion Vulnerabilities (Local and Remote – LFI, RFI): When a web app allows files to be uploaded without proper checks, attackers can use this to their advantage. They can execute harmful files either from their own location (RFI) or from within the server (LFI).
- Exploited Services and Application Vulnerabilities: Sometimes, flaws in the software or services connected to the website can be exploited by attackers to plant web shells.
Once these web shells are in place, they might come loaded with advanced features like encryption to hide from detection or user-friendly interfaces to make it easier for attackers to carry out their malicious plans.
How do web shells function?
Once a web shell infiltrates a server successfully, it appears harmless at first glance. However, it serves as a concealed entrance for attackers. When accessed by the attacker via a web browser, it activates a user interface or a basic command line tool, granting direct control over the server.
This arrangement empowers attackers to carry out a multitude of actions from afar: they can pilfer sensitive data, establish new administrator accounts for sustained access, alter server configurations, initiate denial of service attacks, or utilize the server as a launching pad for subsequent attacks.
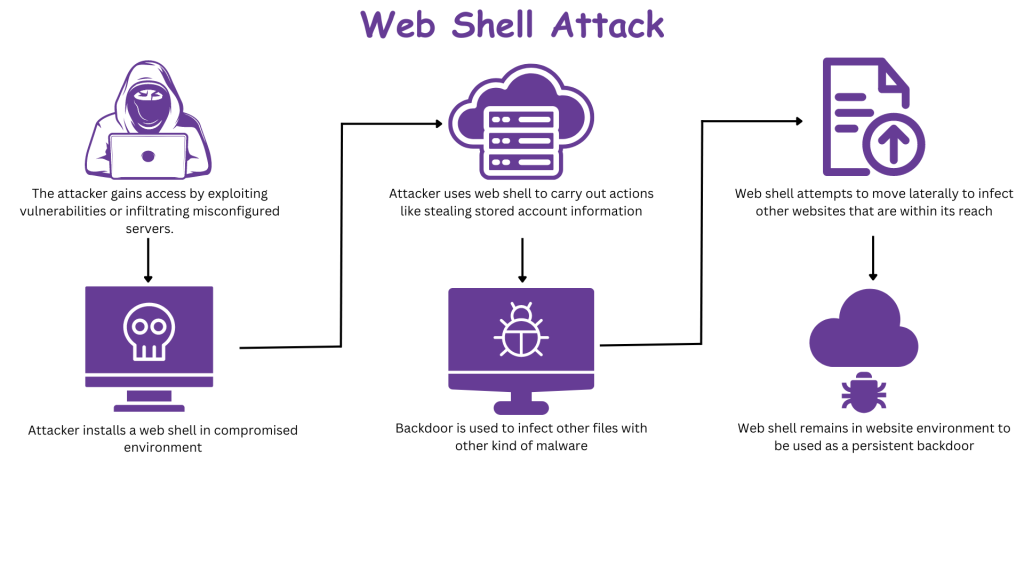
Consider this typical sequence of events for assaults on vulnerable websites:
- The attacker breaches a server with poor configurations or exploits a known software flaw to gain unauthorized entry.
- The attacker implants a web shell within the compromised environment.
- The attacker utilizes the web shell to conduct operations such as stealing stored account information and customer data.
- The backdoor is utilized to contaminate other files with different types of malware, such as credit card skimmers, SEO spam, or remote access trojans.
- The web shell endeavors to spread to other websites within its proximity.
- The web shell lingers in the website environment to serve as a persistent backdoor and sustain unauthorized access.
Detecting web shells can be challenging as they often mimic legitimate files and employ diverse obfuscation techniques to elude security measures. Their capacity for controlling entire servers renders them an especially perilous tool in an attacker’s arsenal.
Types Of Web Shells
Web shells come in different types and serve various purposes. They can be simple tools for running basic commands or advanced systems granting complete control over a hacked server. Knowing the distinctions between these types is crucial for detecting and dealing with threats efficiently.
To simplify the understanding of these malicious programs, we’ve categorized them into three main groups:
Simple web shells
Web shells are like secret doors that hackers sneak into websites to control them. Imagine a hidden panel in a house that only the burglar knows about. These sneaky tools let bad actors run commands on a server, just like controlling a computer remotely. They’re small and tricky to spot, making them a favorite tool for hackers.
These basic web shells may seem simple, but they pack a punch. They can do a lot of damage, like giving the hacker more power, changing files, or even launching other attacks. Think of them as the first step for hackers entering a server.
Here’s a simple example of how they work: the hacker sneaks this tiny script into a website they’ve taken over. When someone sends a command to the script, it runs it on the server. It’s like giving the hacker keys to the back door, letting them get into the website whenever they want.
class XShell {
@param string $command
public function Execute($command) {
$command 2>&1';
$handle popen($command, 'r');
$log = '';
while (Ifeof($handle)) {
$line = fread($handle, 1024);
$log. $line;
}
pclose($handle);
return $log;
}
}
$cmd = $ POST['cmd'];
$Submit = $_POST['Submit'];
if ($Submit) {
$myshell NEW XShell;
//$cmd escapeshellcmd($cmd);
//echo "Command: ". $cmd."<br>";
$output = $myshell->Execute($cmd);
$Submit= "";
//echo "<pre>".$output."</pre>'
}
else {
$cmd = "";
$output = "";
These scripts might be small, but they’re not invisible. Website monitoring tools can catch them in action. They look out for certain functions, like “popen” or “shell_exec”, that these scripts often use. It’s like setting up alarms to catch burglars trying to break in.
Complex web shells
Complex web shells are advanced tools used by attackers to gain control over compromised web servers. These web shells offer a user-friendly interface, often with graphical elements, making it easy for attackers to manipulate files, databases, and even launch further attacks. They come with various features like custom management tools, which help attackers navigate the compromised system and execute sophisticated attacks. However, their complexity and additional features increase the likelihood of detection by security systems if not properly hidden.
These advanced web shells are typically PHP-based and are widely available in hacking communities. Some common examples include WSO, c99, B347K, and r57.
Moreover, the code of these web shells often contains PHP references like “FilesMan,” which can be easily detected by scanning tools. Therefore, it’s crucial for attackers to obfuscate or hide these web shells effectively to avoid detection and maintain access to the compromised server.
session_start();
$password = "";
$passtype = "";
$color = "#df5";
$default_action = 'FilesMan';
Persistent web shells
Persistence in web shells refers to their ability to remain active and accessible even after detection and cleanup attempts. Attackers achieve persistence through various techniques to make sure their malicious code stays on the compromised server. For instance, they might embed backup mechanisms or set up automatic re-upload of the web shell. They might also exploit vulnerabilities in the server to reinstall the web shell automatically.
A common method attackers use is adding a cron job to the website. This cron job runs at regular intervals and simply re-infects the server with the web shell or other malware the attacker wants to deploy.
Persistent web shells are a major concern because they show that the attacker is determined to keep control of the server for the long term. They might want to steal data, install more malware, or use the compromised server as a starting point for future attacks.
Getting rid of persistent web shells isn’t easy. It requires a thorough investigation and strong remediation efforts to find and fix all the vulnerabilities the attacker used to get in and stay in. It’s crucial to ensure that the server is completely clean to prevent further damage or unauthorized access.
Understanding the Dangers and Consequences of Web Shells
The presence of any type of web shell on a server is a big problem that needs to be fixed quickly. Web shells show that someone has hacked into the server, which is really bad for security.
Here are some of the main problems with web shells:
- Unauthorized access: Web shells let attackers get into the server without permission. They can take important information like personal details or financial records.
- Server hijacking: Hackers can use a hacked server to do more bad things, like sending spam emails or attacking other websites.
- Website changes: Attackers might change what a website looks like, which can make people not trust the website anymore.
- Website viruses: Web shells can let in other viruses that can do more damage, like locking up files or spying on users.
- Stealing data: Web shells can secretly take information over time, which is really bad for privacy and security.
- Business problems: Having a web shell can cause big problems for a business, like the website not working, losing money, or getting in trouble with the law.
Because of these problems, finding and getting rid of web shells is really important for anyone in charge of keeping a website safe. It’s important to have good security measures in place and always be looking out for ways hackers could get in.
Web Shell Defense: Methods for Detecting and Removing Web Shells
Detecting web shells on your server can be tricky, as they are designed to hide and blend in with legitimate files. However, with the right approach and tools, you can spot and remove these dangerous threats.
Here are some signs to watch out for:
- Unusual Server Activity: Keep an eye out for any strange behavior on your server, such as unusual processes running or unexpected changes in file permissions.
- Unexpected Web Traffic: If you notice a sudden increase in web traffic or requests to unusual URLs, it could be a sign of a web shell in action.
- Unfamiliar Files: Check your server directories regularly for any files that you don’t recognize or remember adding. Web shells often disguise themselves as innocuous files to avoid detection.
Regularly reviewing your website and server logs can also help you catch unauthorized access attempts, which may indicate the presence of a web shell.
To detect web shells accurately, it’s crucial to use specialized security tools like malware scanners and intrusion detection systems (IDS). These tools can identify known web shells and detect suspicious patterns that suggest malicious activity.
If you do find a web shell on your server, take immediate action to remove it and prevent further damage:
- Isolate Your Server: Quarantine the affected environment to prevent the infection from spreading to other parts of your server.
- Remove the Web Shell: Analyze the web shell carefully to determine the best way to remove it. This may involve manually deleting malicious files and any related components.
- Investigate the Breach: Determine how the attackers gained access to your server and fix any vulnerabilities they exploited. Assess the extent of the damage and take steps to prevent future attacks.
- Restore from Clean Backup: If you have a clean backup of your website, use it to restore any affected files. Make sure the backup is free of malware or backdoors before restoring it.
- Harden Your Security: Update all software on your server, including your content management system (CMS), plugins, and themes. Change your passwords and consider installing a web application firewall to block future attacks.
Dealing with web shell infections can be complex, so it’s often best to seek professional help. HackersThirdEye offers specialized services for cleaning up infections, detecting malicious code, and protecting websites from future attacks.

